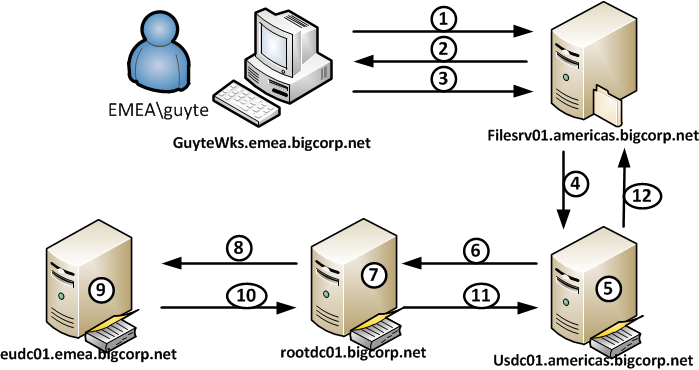
- Client (GUYTEWKS) sends username (EMEA\guyte) to FILESRV01.americas.bigcorp.net
- FILESRV01 generates NTLM challenge and sends it back to the client
- The client sends NTLM response, containing the encrypted user password hash, to FILESRV01
- FILESRV01 passes the authentication request to a DC in the domain it is member of to which it has a secure channel active (USDC01.americas.bigcorp.net in our case)
- The USDC01 DC sees that the authentication request is not for its own domain and consults the trust information. AMERICAS domain does not have a direct trust with EMEA domain, but the forest root domain does, hence the DC in AMERICAS domain decides to rout the request to a DC in ROOT domain
- USDC01 passes the authentication request to a DC in ROOT domain to which it has an active secure channel (ROOTDC01.bigcorp.net)
- ROOTDC01 receives the request, but can not authenticate it locally. Fortunately ROOT domain has a trust with EMEA domain and ROOTDC01 routs the request to a DC in EMEA domain
- ROOTDC01 passes the authentication request to a DC in EMEA domain to which it has an active secure channel (EUDC01.emea.bigcorp.net)
- EUDC01 sees that it can authenticate the request locally and verifies the credentials.
- We are going all the way back (the way we came from) to FILESRV01 to tell it whether the authentication attempt was successful
Read the webpage in PDF:[wpdm_file id=79 title=”true” ]